
Apple’s AirTag is an odd product from a company that typically makes devices designed for interaction. It’s an inert button designed to be tracked passively across Apple’s crowdsourced Find My network, in which every iPhone, iPad, and Mac that opts into the Find My network provides privacy-protecting location information about wayward hardware.
Because AirTags are small, easy to conceal, and have a long battery life, they’re ideal for those of us who accidentally leave things behind, lose our keys, can’t find our car in a parking lot, or worry about having stuff stolen. With an iPhone 11 or 12, you can easily find an item attached to an AirTag around the house, too.

AirTags contrast sharply with GPS-based tracking devices, often used to keep tabs on people with dementia and track children. Such GPS devices work best outdoors, require frequent charging, are somewhat bulky (relative to an AirTag, at least), and have a recurring service fee. (The competing Tile products have the same advantages as AirTags, but Apple’s network of nearly a billion devices on its Find My network gives it a leg up in ubiquity. Of course, that ubiquity introduces safety concerns, too.)
We’ve written previously about the Find My network in general and how it works, Apple’s move to expand access to third parties, and the introduction of the AirTag. See:
- “How Apple’s New Find My Service Locates Missing Hardware That’s Offline,” 21 June 2019
- “Apple Opens “Find My” Crowdsourcing to Third-Party Accessories,” 9 July 2020
- “Apple Opens “Find My” Crowdsourcing to Third-Party Accessories (For Real This Time!),” 7 April 2021
- “Apple’s AirTag Promises to Help You Find Your Keys,” 20 April 2021
Now that I’ve had a chance to experiment with some AirTags, and Apple has released specifics on the intention and limitations of tracking, this article focuses on scenarios that attempt to think through the consequences of how people will use and misuse AirTags. There are many terrific ends to which AirTags will be put, and I believe those represent the vast majority of cases of how they’ll be used.
But Apple built in privacy for both the people who own AirTags and those who find an AirTag near them, including anti-stalking measures. These choices may prevent both legitimate and illegitimate uses. I get into the technical details in the latest version of Take Control of iOS & iPadOS Privacy and Security, with a significantly revised chapter on the Find My network and complete details on pairing and using AirTags, as well as other Apple hardware.
In this article, however, let’s dig into how people will use AirTags, starting with items that are lost, moving on to items that are stolen, and finishing with thoughts about stalking.
Something Lost
Bill’s Wayward Keys
Bill can never find his keys. He knows he should pick a consistent place to put them down or mount a hook inside the front door. Instead, he leaves them in a coat pocket, plops them on a table and drops mail on them, or somehow leaves them somewhere unexpected—like the bread drawer?!
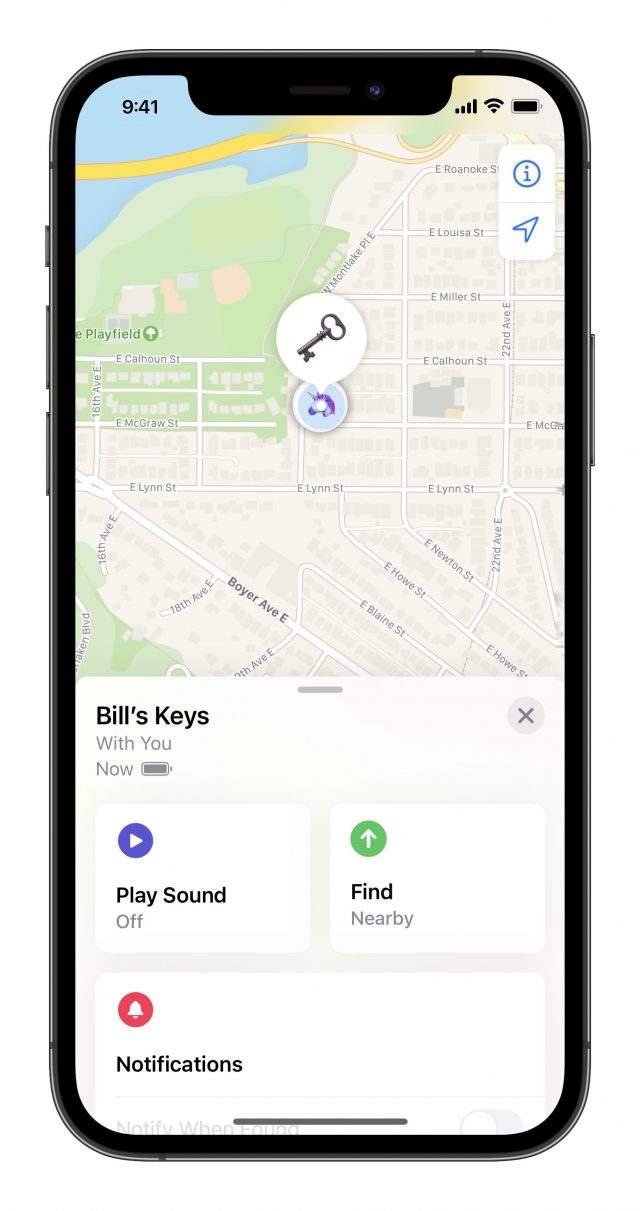
Like this morning, when he searched fruitlessly after finishing breakfast. But this time, Bill had an AirTag attached to his keychain and an iPhone 11 Pro. He launched the Find My app, selected his keychain AirTag, and tapped Find Nearby. The Find My app started listening for the ultrawideband broadcast from his AirTag. Once it locked on, Bill walked around his home, looking like he was dowsing for water, as the Find My app nudged him in the right direction and lit up green when he was on track.
The app showed the distance as he closes in on his AirTag and displayed “here” when he was on top of it. He still couldn’t see it, so Bill tapped the speaker icon, and the item played some pleasant, recognizable tones to provide a little more guidance. Ah, there it is! Under the jean jacket in the pile of laundry.

Should Bill have been too far from the AirTag, or if there were too many obstructions in the way—like walls, books, or laundry—Find My would have picked up the more powerful but non-directional Bluetooth signal and provided some general directional aid. As he got closer, he could try tapping Find Nearby again to see if the ultrawideband signal could reach his phone.
Manjula and the Missing Messenger Bag
Meanwhile, Manjula knew she put her messenger bag down somewhere after setting out to drive home, but she wasn’t sure where. She remembered that she had it with her in the car but couldn’t seem to find it in the house. Fortunately, she had an AirTag zipped into a pocket for just this reason.
She brought up the Find My app on her phone and tapped her bag’s AirTag. It showed up on a map a couple of blocks away, where she parked her car, with the most recent update just a few minutes before. “Of course!” she thought, “I never brought it in!”
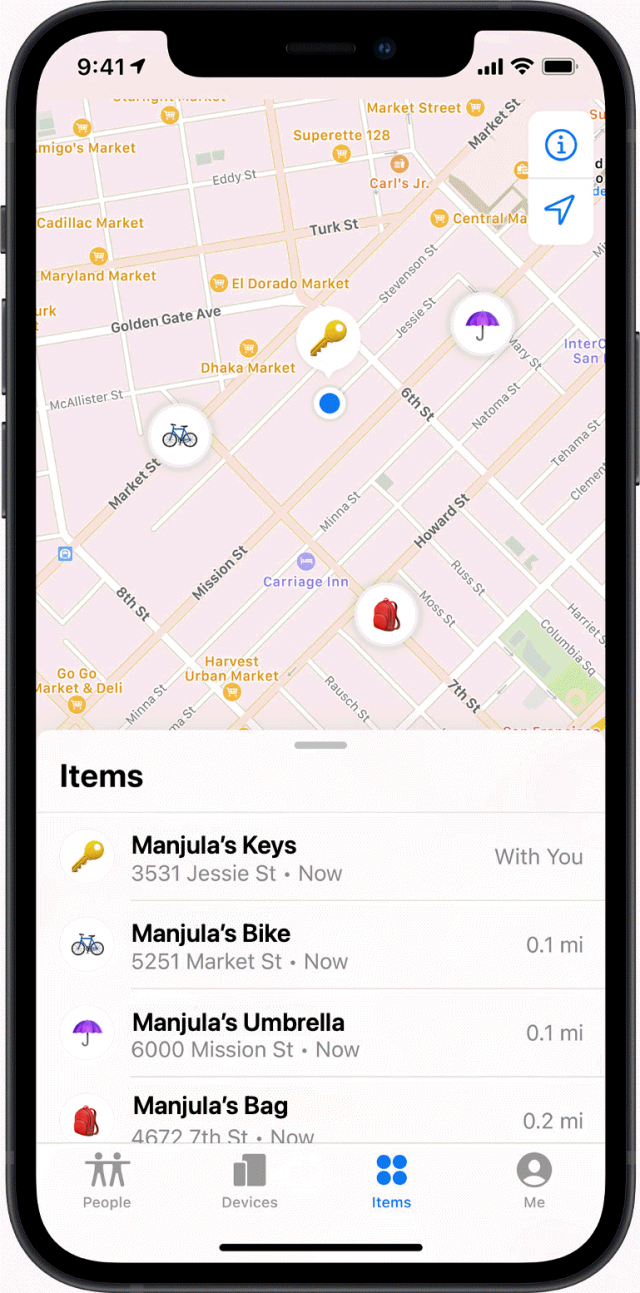
While AirTags rely on ultrawideband and Bluetooth for nearby location finding, enough people carrying iPhones had passed by Manjula’s parked car that the Find My network updated the position.
Nic’s Missing Laptop Bag
Across town, Nic was slightly frantic. They can’t figure out where their laptop bag is. The college student wondered: “Did I leave it in the library? At the coffee shop? In my friend’s room? On the tram? Aieee!”
Firing up Find My, Nic didn’t see a recent location for their laptop bag’s AirTag, so they tapped Enable under Lost Mode and entered their phone number. Through troubled sleep, they wondered if their computer was gone for good. But a phone call woke them up in the morning with good news: a library staffer found their bag while opening up the library. Because the staffer only had an Android phone, the AirTag wasn’t able to update its location with the Find My network.
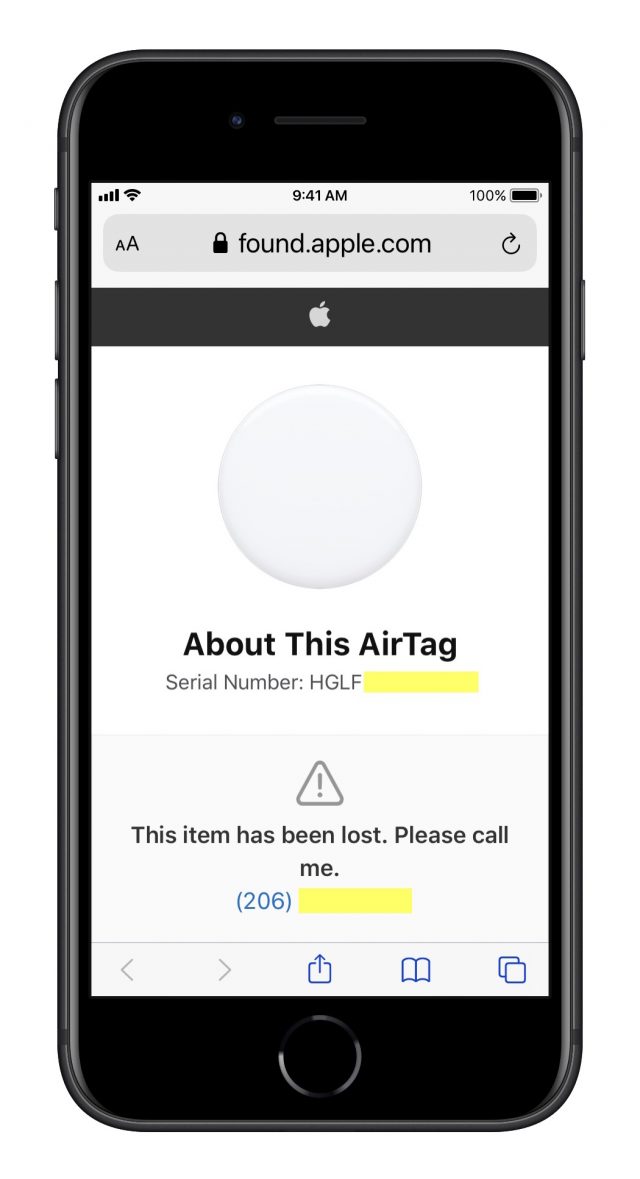
However, the library staffer looked through the bag for ID, found the AirTag, and held it up to their Android phone, which read the AirTag’s RFID tag over NFC (near-field communication). The staffer then followed the link that the Android phone displayed to the AirTag’s serial-number page and called the number Nic had posted. Nic arranged to get it later from lost-and-found and fell back into a dreamless slumber.
Martyn’s Post-Bender Panic
Speaking of slumber, Martyn woke blearily after a bender with his friends. While he got home safely after getting a ride from a friend who hadn’t been drinking—and avoided making a mess in the backseat—he couldn’t find his jacket, which had his money, wallet, and other important possessions zipped into it, along with an AirTag. He had no memory of where he wound up as the previous night progressed.
Martyn’s iPhone rang—at least that was in his trouser pocket. It was his friend Rafael, who was driving around when his iPhone displayed an alert that an AirTag was “moving” along with him. He tapped the notification, tapped Play Sound, and found Martyn’s jacket balled up under the passenger seat. “Do you want it back now?” Rafael asked. Whew!
Ruth Bader Ginspurr Escaped the House
Tracy was despondent. Her cat, Ruth Bader Ginspurr, had apparently slipped out the door when nobody was watching. She was not an outdoor cat, and the last time she’d gotten out, it was a week before a neighbor found her, hungry, pitiful, and worse for wear.
Ruth wore ID tags, but Tracy had also recently equipped her with a collar designed to hold an AirTag. In the Find My app, she saw that Ruth’s AirTag was most recently seen in a grove of trees in a park full of iPhone-toting runners. With Ruth’s favorite squeaky mouse in hand, Tracy went to the park, squeezed the toy a few times, and spotted Ruth—and grabbed her for the walk home.
Something Stolen
Chai’s Snagged Bag
It was only a minute. After waiting two weeks after her second COVID-19 vaccination shot, Chai had ventured out to sit in a café for the first time. She set her bag down under a table for a moment in a mostly empty coffee shop and went to wash her hands. When she came back, the bag was gone. The barista had been leaning down to clean the espresso machine and didn’t notice someone come in and snatch it.
Chai’s MacBook Air, sketchbook, and various sundries were in the bag, along with an emergency $20 bill and an AirTag, but she had taken her phone with her to the restroom. She pulled up the Find My app, marked the AirTag as lost, and watched for updates. Minutes later, she received a ping. She thought about calling the police but figured they wouldn’t come fast enough to help and decided to look for the bag on her own, promising herself that she wouldn’t put herself in potential danger by getting too close.
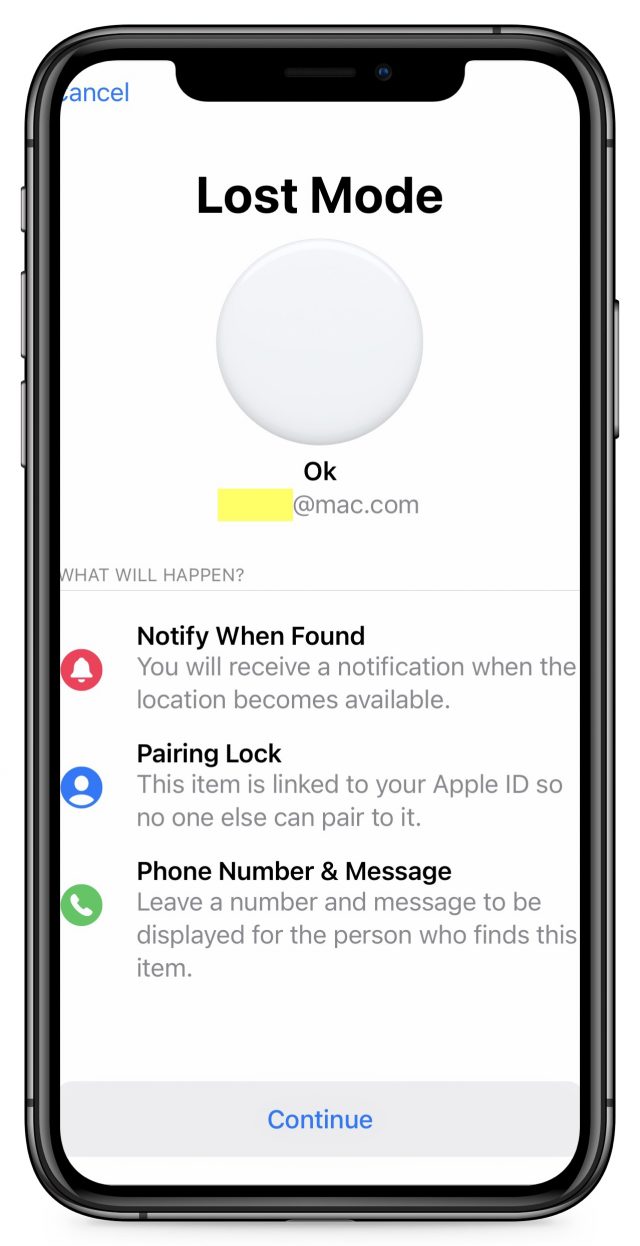
As she approached the location marked on the map, she tapped Find Nearby and started to get location information. Surely it couldn’t be down an alley? And that seemed dangerous. But when she got closer, she realized her bag was on the ground, and there was nobody nearby. She grabbed it and found that her MacBook Air and emergency cash were gone, but the sketchbook and everything else remained in place. She used Find My to send a signal to erase her MacBook Air, should the thieves connect it to the Internet again, and called her insurance company.
Sorry, Charlie
Charlie was less lucky. His backpack containing an AirTag was taken by someone who spotted an open window, climbed up part of a wall, and grabbed it out of his house. He could see briefly where it went in Find My, but then it disappeared. He never found the backpack or received any tracking updates, so he assumed the thief was clever enough to search the backpack and either remove the AirTag battery or smash it.
Fenchurch’s Double AirTag
Fenchurch left not one but two AirTags in her car. Living in a city with a high rate of car theft, she thought perhaps hiding AirTags could be an extra deterrent in addition to the car alarm, the electronic ignition–disabling technology, and the steering wheel lock. Sadly, her car was stolen—but her bet was good. The AirTag that she’d placed in the glove compartment, where it was easily found, must have been tossed out the window since Find My helped her find it in the mud on a parking strip.
But she’d hid the other AirTag with the spare tire. She assumed the thieves didn’t receive alerts that would have made them aware of the AirTag’s presence—they must not have owned iPhones—but enough people passed nearby to produce location updates. Fenchurch called the police, who became interested when they realized that the car was ostensibly located in a seedy industrial area. They checked out the address and were able to recover Fenchurch’s car while shutting down the chop-shop operation.
Bad News, Vicente
The hidden AirTag strategy worked for Fenchurch, but Vincente had less luck. He had taped an AirTag to the underside of his dashboard, figuring it would be hard to find. However, the thieves who stole his car one night must have been carrying an iPhone that was recent enough to display an alert.
He deduced that because when he woke up, even before he could mark the AirTag as lost and call the police, he saw that the location in the Find My app of the AirTag was several blocks from the parking lot where he’d left it, tagged with a timestamp of 11:53 PM the previous evening. While waiting for a call back from the police, he went to the location on the Find My map, and his car wasn’t there—nor was an AirTag lying on the ground. He figured the thieves received an alert about an unknown AirTag “moving” with them as they drove off in the purloined vehicle. They probably then found and destroyed the AirTag before any other iPhone could reveal its location.
Whatever the case, the AirTag never appeared again. Nor did his car!
Someone Stalked or Tracked
Yuen’s Ex-Boyfriend
“Where was that beeping coming from,” Yuen wondered. He couldn’t figure out what he owned that could be making the noise. He finally unzipped and emptied out every last pocket in his backpack—and discovered something he didn’t remember. A small bag, cinched tight. When he opened it, he found a round button with an Apple logo.
Searching via Google, Yuen discovered it was an AirTag—and that he could scan it with his Android phone. When he tapped it to his phone to view the associated Web page and realized what it was being used for, his blood ran a little cold. Was this planted by his jealous ex-boyfriend? The controlling person he broke up with for just this sort of reason? Yuen noticed the link Apple provided about contacting law enforcement.
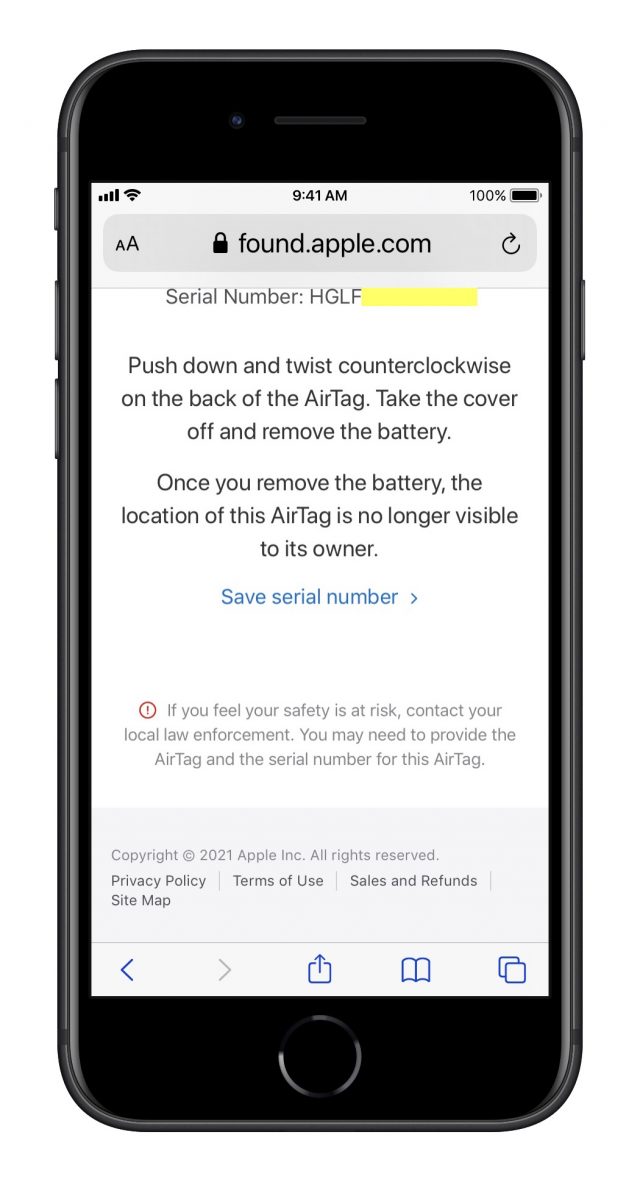
With the help of a law clinic and local police, Yuen was able to prove that his ex had purchased the AirTag—the serial number helped—which led to charges and a restraining order.
Annelise’s Nosy Neighbor
Annelise had had enough. A neighbor kept conveniently showing up “accidentally” at regular intervals in other parts of town when she went out for coffee, to meet a friend, or to shop. It was too much, and she suspected that she was being stalked. She had read online about how her iPhone could be used to track her and consulted some technical friends, too. But between her online research and her friends’ analysis, it didn’t seem to be hacked. Sometimes she left her iPhone at home and just relied on her Apple Watch, and the neighbor still appeared.
Then she realized she ran into the neighbor only when she drove somewhere, not when she walked, biked, or rode with someone else. With the help of a friend and a Bluetooth-scanning app for her iPhone (like BLE Scanner), she scoured her car and eventually found an AirTag hidden inside the lining of one of the seats. “Well, that’s creepy,” she thought. She must have left the car unlocked at some point, allowing him an opportunity to hide the AirTag inside—or, worse, he’d broken in without her knowing.
Reading up on Apple’s website, Annelise thought that she should have been notified or that the AirTag would have made a sound at various times. But after checking her iPhone’s settings, she realized that she had disabled the Find My network option in Settings > Account Name > Find My > Find My iPhone. When Apple added the Find My network in iOS 13, she was weirded out by the thought of participating in a global tracking network. But that choice also meant her iPhone wasn’t monitoring for AirTags that traveled with her.
And, because Annelise parked her car near both her house and the neighbor’s, the AirTag reassociated at least once a day with the neighbor’s phone. If she had taken an extended trip with her car, the AirTag might have started beeping. Due to the pandemic, she rarely drove anyone in her vehicle, so no friend with an iPhone would have seen the alert, either.
She was about to move out of town in any case, and she decided to leave her apartment and stay at a friend’s place for the remaining time she had—after she removed the AirTag, visited the police station, and filed a report.
A Package for Betsy
Betsy had never liked people she didn’t know well having her home address. She was a private person and had had incidents with over-eager boyfriend and girlfriend wannabes. Nothing terrible, but it still put her off having her address in circulation. So she used a package-delivery storefront for her mail, which provided the added benefit that her packages were never stolen from her apartment building’s mailbox area.
But one day, she picked up a small box from an unknown sender. When she brought it home and opened it, she found it contained a relatively expensive purse she’d mentioned on Facebook but felt she couldn’t afford. A secret admirer who asked around for her address and got it from a friend?
While checking out the purse, she felt an odd lump. Sewn into the lining was an AirTag. She knew what it was from Apple’s marketing and found the experience unsettling. Someone could have known when she arrived at the package store, her path home, and where she lived. Who would do that?
She looked up the AirTag’s serial number, removed its battery, and decided against calling the police for the time being. But she did post a subtle message on Facebook that made it clear she’d found the tracker and was perfectly capable of taking the next step to identify the sender. Fortunately, nothing ever came of it.
Florian’s Mystery AirTag
Florian had a disturbing message pop up on his iPhone: “AirTag Found Moving with You,” with the annotation “The location of this AirTag can be seen by the owner.” He panicked for a moment. Who wanted to know where he was? Why was someone keeping tabs on him? He tapped the notification, and a more complete message appeared, including the first time the AirTag was found near him—1:30 PM—and the message that it “may be attached to an item you are borrowing.”
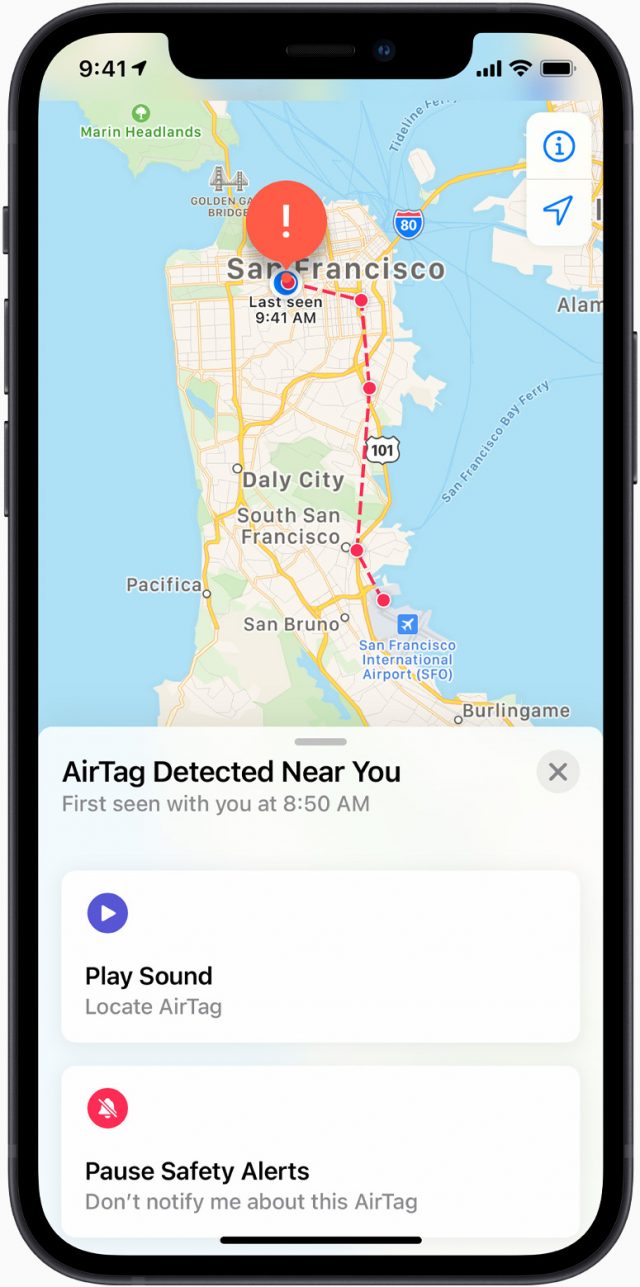
“D’oh!” Florian slapped his forehead. He had borrowed a duffel bag from his friend Asok. He looked inside a zipped pocket, and there was an AirTag. He texted Asok: “Busted! Dude, you’re tracking me!” Asok texted back an emoji of a tongue sticking out and the message, “Sorry! I forgot I always leave that in there!” Florian tapped Continue on his phone and tapped to disable notifications for a day.
Better for Some Uses Than Others
I’m just scratching the surface of the cases in which AirTags will be used and abused. It seems clear that Apple needs to refine some of the features in the system. The length of time before an AirTag makes noise, how quickly you’re alerted to an AirTag traveling with you, and the fact that a setting can disable such alerts all need more thought.
Some of the gaps in knowing whether you’re being tracked are large enough to enable abusive behavior that Apple wants to prevent. The Washington Post’s Geoffrey Fowler tested being tracked with permission, and he found a number of loopholes and exceptions that clever stalkers and abusers could exploit.
On the plus side, the record keeping and association of AirTags to individuals makes it relatively easy to figure out who owns an unwanted tracker and what behavior that person has engaged in. A stalker would, at a minimum, have to create a throwaway iCloud account and use it with a disposable iPhone or iPad to track an AirTag to avoid creating an overt trackable connection. That’s a lot of money and effort, and it might still be difficult to avoid providing identifiable information unintentionally. (Abusive people aren’t always great at anticipating consequences, but some are keenly aware of how readily they can be identified.)
AirTags also don’t help much when it comes to deterring or tracking theft. They aren’t a deterrent because they have to be hidden to avoid being destroyed. And when it comes to tracking a stolen item, the combination of iPhone alerts and general suspicion will probably result in the thieves finding and destroying the AirTag in quick order. Though, as I pointed out above, you might be able to recover a stolen bag minus its cash and electronics.
Happily, Apple seems to have designed the system to be open to adapting, maturing, and improving. The overwhelming majority of uses of AirTags and the Find My network will certainly be positive ones. The goal will be to block malicious uses more effectively without diminishing the value of the entire system.
