MacTalk
January 2023

Apple’s Advanced Data Protection Gives You More Keys to iCloud Data
Critics of cloud services often point—with a bit of finger-wagging—at the fact that cloud-stored data is theoretically vulnerable to being stolen by bad guys and handed over in response to government requests. That’s true even if the data is encrypted in transit to and from user devices and at rest on the company’s servers as long as the company maintains the encryption key necessary to decrypt the data.
The solution is conceptually simple—allow the user to generate and control all the encryption keys, a technique called end-to-end encryption. When that’s true, the data is unreadable to anyone other than the user. Risks of eavesdropping, theft, and government overreach are greatly reduced. However, the user then has the ultimate responsibility to remember and protect those keys, and if something goes wrong, there is absolutely no recourse—without the appropriate key, the data is effectively gone. And yes, that happens all the time, much as with the people who forget their crypto wallet password and lose millions in funny money.
For some time, Apple has provided end-to-end encryption for 14 of the 26 types of iCloud data, including Health data, Passwords and Keychain, Apple Card transactions, and more. You may not realize that you control the encryption keys for those data types because Apple has integrated them into the overall security infrastructure underpinning its devices, operating systems, and online services. That’s why it’s so important to remember your iPhone/iPad passcode and Mac login password.
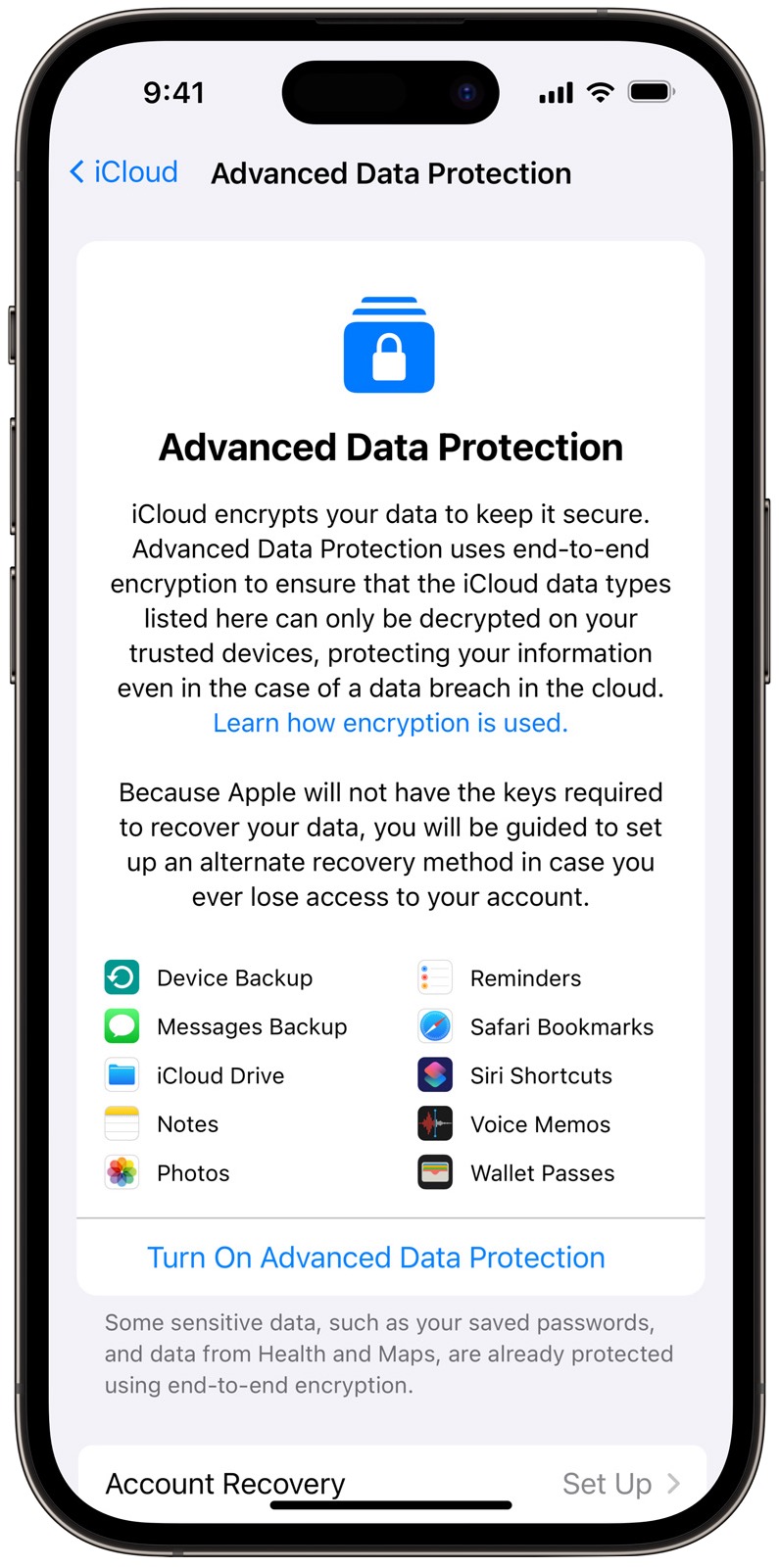
But for the twelve remaining types of iCloud data—iCloud Mail, Contacts, Calendars, iCloud Backup, iCloud Drive, Photos, Notes, Reminders, Safari Bookmarks, Siri Shortcuts, Voice Memos, and Wallet passes—Apple stores the encryption keys in Hardware Security Modules in its data centers.
For iCloud Mail, Contacts, and Calendars, the need to interoperate with external email, contacts, and calendar systems requires that Apple manage the encryption keys. For the other nine, Apple’s control of the encryption keys enables the company to recover data for users who forget their passwords and have no fallback. (In such a situation, the end-to-end encrypted data types are lost.) But, of course, it also theoretically leaves that data vulnerable to hackers and law enforcement. iCloud Backup, which includes the encryption key for the otherwise end-to-end–encrypted Messages in iCloud, and Photos are the main data types to worry about in that list.
Very soon, those concerned about Apple holding their encryption keys will have some relief.
Enter Advanced Data Protection
Apple has announced Advanced Data Protection for iCloud, a major upgrade to iCloud security that provides end-to-end encryption for the nine data types previously mentioned. Advanced Data Protection is optional—you must explicitly enable it—because it prevents Apple from recovering your data. That seems like a reasonable tradeoff because the people who are the most likely to forget their passwords and need recovery help from Apple are probably less likely to have problems with hackers or law enforcement.
When you set up Advanced Data Protection, you’ll be prompted to set up alternate recovery methods, such as an account recovery contact or a printed recovery key, and you must set up at least one. Apple isn’t going to make it easy for you to lose your data.
Luckily, it’s not a one-way street. If you ever decide that you’d prefer Apple’s recovery help to end-to-end encryption of things like iCloud Backup, you can turn Advanced Data Protection off with no data loss.
There are several technical consequences associated with enabling Advanced Data Protection beyond it not protecting iCloud Mail, Contacts, and Calendars:
- iCloud.com Web access: Turning on Advanced Data Protection automatically disables Web access to data at iCloud.com due to Apple’s keys having been invalidated. You can turn Web access back on using a trusted device, but every visit to iCloud.com requires authorization from a trusted device, and the connection passes only normally accessible iCloud.com data (not Health, for instance) and only for an hour. If you make heavy use of iCloud.com, Advanced Data Protection may be burdensome.
- Data sharing: When you share notes, reminders, and iCloud Drive folders or use iCloud Shared Photo Library, all the data remains end-to-end encrypted and available only on the participants’ devices as long as all users involved in sharing have Advanced Data Protection turned on. Sharing with anyone who’s not using Advanced Data Protection or using the “anyone with a link” option when sharing makes the content available to Apple servers using Apple-controlled keys.
- Collaboration: The iWork collaboration capabilities and the Shared Albums feature of Photos don’t support Advanced Data Protection. The real-time collaboration in iWork requires server-side mediation to coordinate document changes, so Apple has to maintain those keys. Since Shared Albums can be publicly shared on the Web, Apple also has to manage keys for that data.
- Third-party apps: Developers whose apps share data via iCloud must mark CloudKit fields as encrypted to have them protected by Advanced Data Protection, and it automatically protects all CloudKit assets.
- Metadata: For iCloud interface and optimization reasons, Apple retains the keys for some metadata associated with iCloud data types that are otherwise protected by Advanced Data Protection. That includes, for instance, the name, model, color, and serial number of the device associated with each backup and a list of apps and file formats included in the backup. Apple says it is working to include more metadata in Advanced Data Protection.
Advanced Data Protection Requirements and Timing
To enable Advanced Data Protection, your account must have two-factor authentication enabled for your Apple ID and a passcode or password set on your devices. Apple says that over 95% of active iCloud accounts use two-factor authentication. (And if you don’t have a passcode on your iPhone for some unfathomable reason, set one immediately. I’m looking at you, Alex.)
More problematic is Advanced Data Protection’s requirement that all devices where you’re signed in with your Apple ID must be updated to iOS 16.2, iPadOS 16.2, macOS 13.1, tvOS 16.2, watchOS 9.2, or the latest version of iCloud for Windows. That’s because older versions wouldn’t know to maintain newly created keys on the device and would try to upload them to Apple’s servers in what the company calls “a misguided attempt to repair the account state.” As a result, you’ll have to sign out of iCloud on any device too old to upgrade to the necessary operating system version. (This requirement may be a deal-breaker for me since I have numerous elderly devices that remain in some level of use.)
Unsurprisingly, Advanced Data Protection is available only for regular Apple IDs. Managed Apple IDs (for employees to use for business purposes or instructors and students to use for educational purposes) and child accounts can’t enable the option.
Apple says Advanced Data Protection for iCloud is available now for those testing betas of Apple’s operating systems and will be available for all US users by the end of 2022. It will start rolling out to users in the rest of the world in early 2023 and may be available worldwide by the end of 2023.
Downstream Effects of Advanced Data Protection
In an interview with Joanna Stern of the Wall Street Journal, Apple’s Craig Federighi said that the global release would include China, and he hadn’t heard complaints from the Chinese government, which generally frowns on technology that prevents state surveillance. It doesn’t seem inconceivable that China allowed Apple to provide Advanced Data Protection in exchange for a China-specific tweak in the recent iOS 16.1.1, which limits AirDrop from being accessible to “Everyone” for more than 10 minutes (AirDrop was being used by protesters). Betas of iOS 16.2 include the same change for all other iPhone users, which, while nominally a loss of functionality, would prevent random creeps from using AirDrop to send nudes to nearby iPhone users.
Finally, you may also remember the furor surrounding Apple’s botched 2021 proposal to scan on-device images for CSAM—child sexual abuse material. Those perturbed by the privacy implications of Apple’s CSAM-detection proposal called instead for the company to live up to its privacy promises and implement end-to-end encryption for iCloud Photos. Advanced Data Protection does just that, raising the question of the status of Apple’s CSAM plans and prompting an update from Apple.
It seems that I was correct with my second suggestion in “Apple Delays CSAM Detection Launch” (3 September 2021)—that the delay was “a face-saving way for Apple to drop the technology like the hot potato it became.” Apple told Wired (emphasis mine):
After extensive consultation with experts to gather feedback on child protection initiatives we proposed last year, we are deepening our investment in the Communication Safety feature that we first made available in December 2021. We have further decided to not move forward with our previously proposed CSAM detection tool for iCloud Photos. Children can be protected without companies combing through personal data, and we will continue working with governments, child advocates, and other companies to help protect young people, preserve their right to privacy, and make the internet a safer place for children and for us all.
Apple also said it wasn’t ready to announce a specific timeline for expanding its Communication Safety feature, but it is working on enabling Messages to detect nudity in transmitted videos when protection is enabled.
Overall, Advanced Data Protection seems like a major positive move on Apple’s part. Once it ships, I’ll give it a try and see what the practical effect is on old devices that can’t run the latest operating systems.
Website design by Blue Heron Web Designs