MacTalk
February 2023

iPhones and iPads Now Require a Passcode on Every Backup/Sync
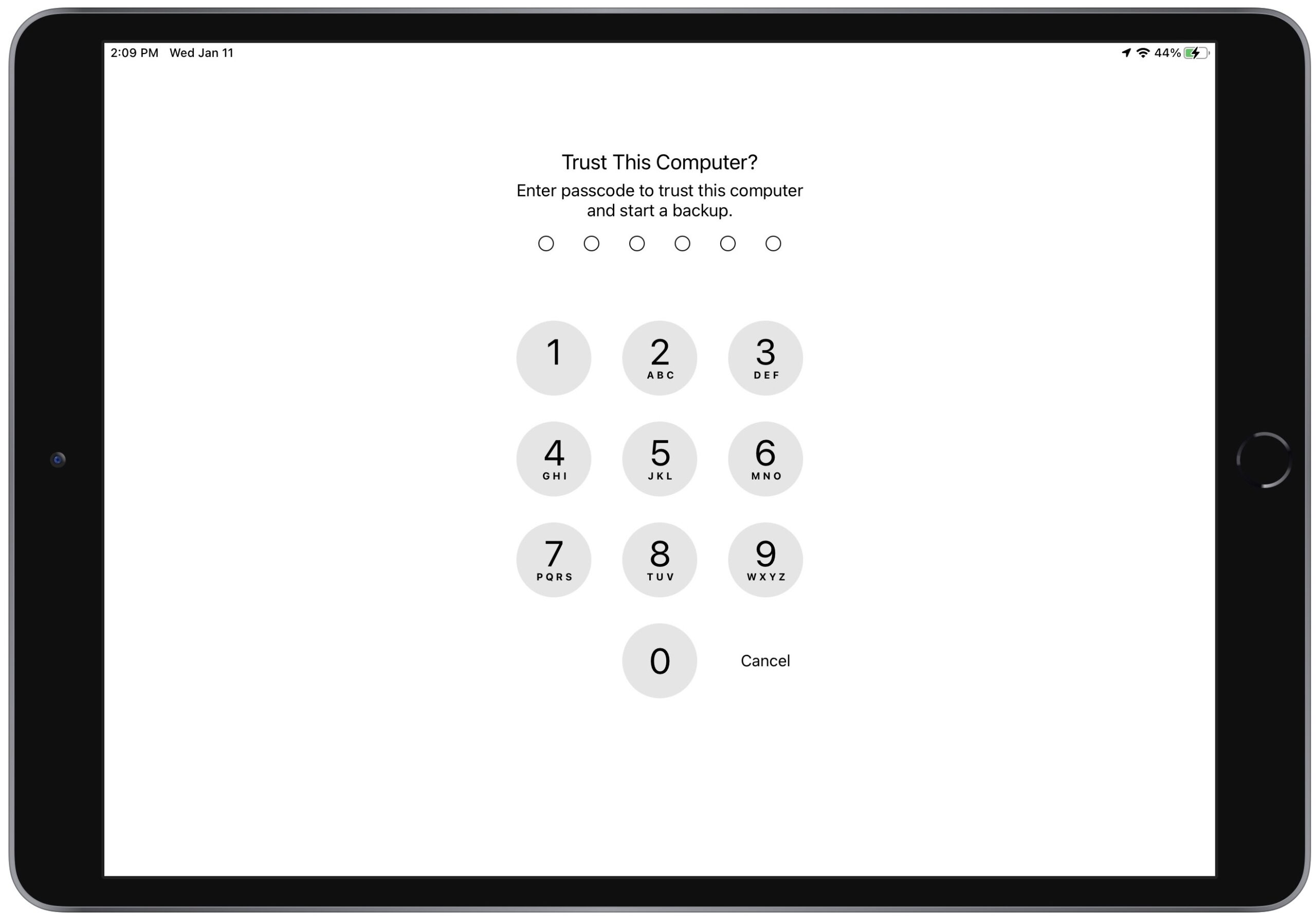
Back in late October 2022, annoyed reports started to appear on TidBITS Talk complaining that connecting an iPhone or iPad to a Mac to back up or sync abruptly began to require entering the device’s passcode every time. The “Trust This Computer?” passcode prompt appeared whether connecting via USB or Wi-Fi. It also appeared when using the iMazing utility to trigger iOS device backups. Before this change, your device prompted for its passcode only when it was freshly set up and hadn’t yet connected to the Mac or when you connected to a new Mac. (It’s also possible you would get the prompt after a major change, but that wasn’t documented or consistent.)
An iMazing blog post explains the situation. In iOS/iPadOS 16.1 and iOS/iPadOS 15.7.1, Apple started prompting on every connection in response to a vulnerability reported by security researcher Csaba Fitzl. In short, Fitzl showed that an attacker with physical access to your Mac and device could use macOS’s AppleMobileBackup command-line utility to trigger a backup to an unprotected location. Since local iOS/iPadOS backups lack encryption unless you add a password, the attacker might be able to extract user data from the relocated backup.
It’s vanishingly unlikely that this would ever happen to most people: someone would have to have access to your unlocked Mac, your device, and the knowledge to run the exploit. It’s the kind of vulnerability leveraged by government agents, criminals, and others with either state-authorized license or nefarious intent.
Instead of preventing AppleMobileBackup from backing up to custom locations without additional permission, Apple chose to mitigate the vulnerability by forcing the user to enter the device’s passcode on every backup or sync connection. And it works: Apple’s new approach prevents the backups from being directed to an unprotected location unless an attacker knows your device’s passcode. If they know the passcode, there’s far worse that they could do with your iPhone or iPad and the data stored on it.
Unfortunately, Apple’s solution is particularly ham-handed because it adds a non-trivial step to every USB or Wi-Fi connection attempt by everyiOS/iPadOS user who backs up or syncs locally. iCloud backups don’t suffer from this requirement, but they require an Internet connection, might use cellular data, and often need an iCloud+ subscription for the requisite storage space. Some people also don’t want to trust Apple’s iCloud security, although the release of Advanced Data Protection should reduce that concern (see “Apple’s Advanced Data Protection Gives You More Keys to iCloud Data,” 8 December 2022).
More troubling is the way that these nonstop passcode prompts will desensitize users to entering their passcodes when asked. The more you’re asked for a password or passcode, the less attention you pay, increasing the chances that you’ll fall for a deceptive prompt from malware attempting to steal your credentials.
Apple’s solution is also overkill. As noted, the likelihood of an attacker with sufficient skills having physical access to a normal user’s Mac and iPhone or iPad is extremely low. The solution is also quite different from Apple’s usual approaches to mitigating risk from physical attacks, which generally offer ways to enable or escalate the level of resistance depending on your needs. A motivated attacker would be more likely to figure out how to encapsulate the exploit into malware that would then exfiltrate user data from the device backup, a valuable vector that would probably be sold to a government for a highly targeted attack. Yes, Apple’s security engineers should address this vulnerability, but they should do so in a way that doesn’t worsen the general user experience.
Practically speaking, you can suffer with entering the passcode on every backup—it doesn’t prevent you from making backups but breaks automated backups with iMazing and may cause you to back up less often. For most people, however, I recommend iCloud backups because they happen automatically, without any human interaction. Nor do they consume space on your Mac, which can be significant, particularly if you have multiple devices with lots of data.
Frankly, I was unimpressed with the overall user experience of the Mac-based device backup workflow. While experimenting with local backups for this article, I had to pull the plug on my iPhone 14 Pro backup before it zeroed out the free space on my Mac. My iMac’s 1 TB SSD had about 150 GB free after backing up 32 GB from my 10.5-inch iPad Pro, and it was happy to start backing up my iPhone 14 Pro, which has about 112 GB used. Unfortunately, the backup wasn’t complete when macOS warned me that my disk was almost full with less than 3 GB available. The numbers should have worked out but clearly didn’t, in yet another example of why free space is difficult for even Apple to calculate.
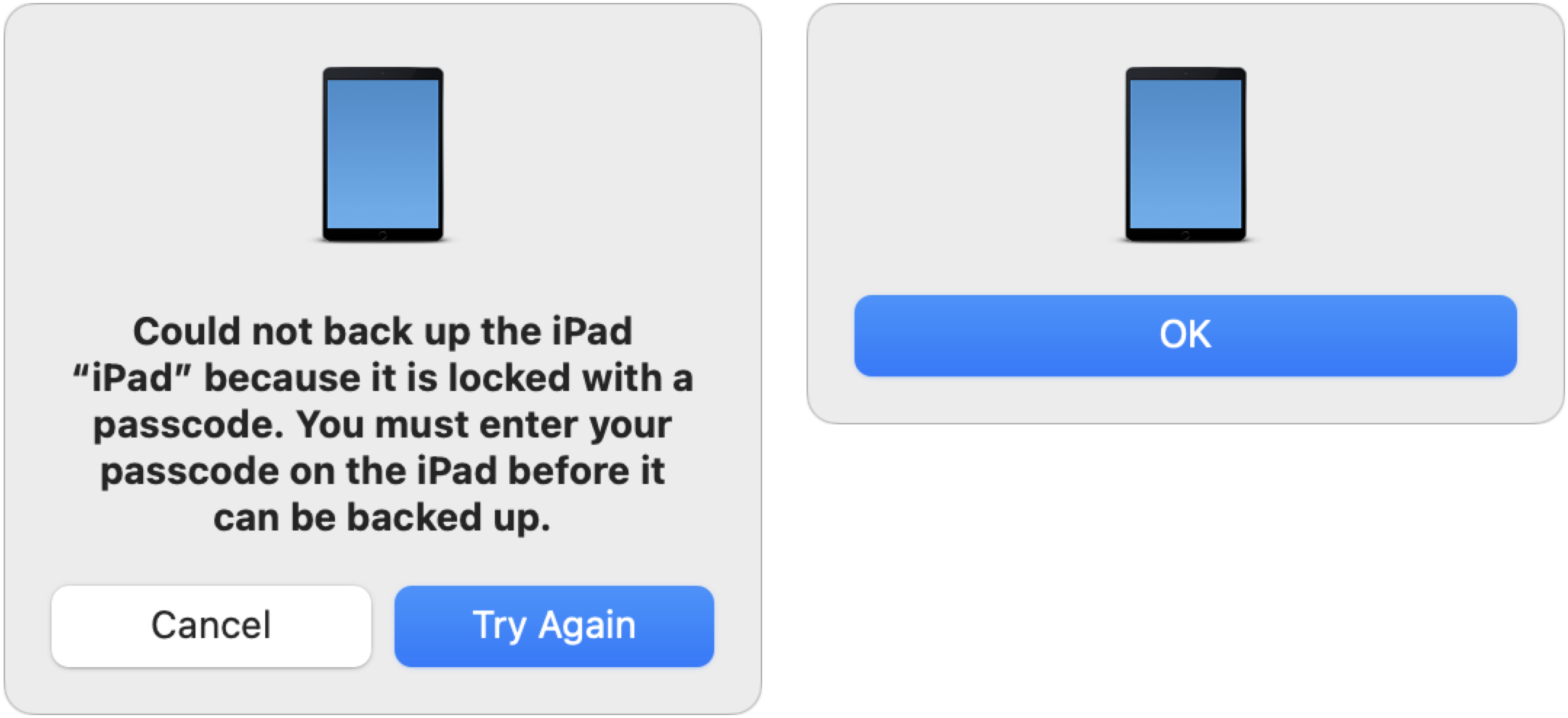
Plus, when I canceled one of the “Trust This Computer?” prompts on my iPad, the Finder displayed the dialog on the left below. Since I didn’t want to try again, I clicked Cancel and got the dialog on the right. Talk about amateur hour!
What I didn’t realize until Shamino mentioned it in the comments is that canceling the “Trust This Computer?” prompt prevents the backup from happening, but allows the sync to continue. That’s functionally helpful but confusingly obscure.
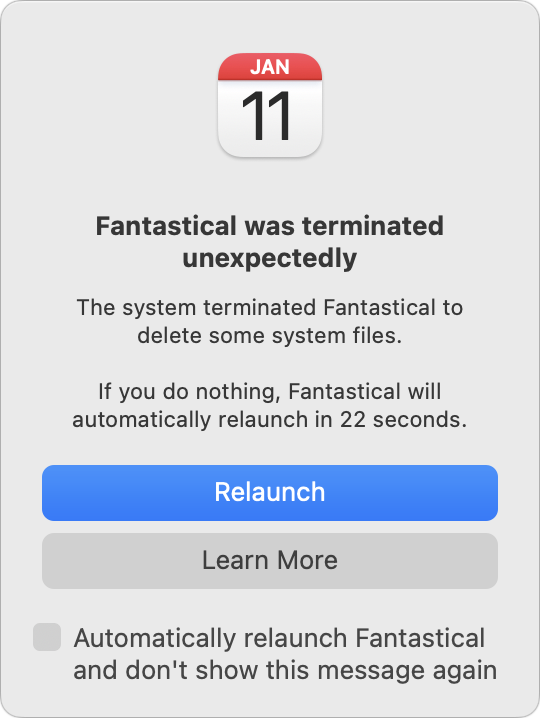
Finally, even though macOS failed to calculate the amount of free space correctly in the end, it did realize it would have to reclaim purgeable space by deleting unnecessary files. That’s expected behavior, but it can cause problems for apps, such as Fantastical, which alerted me that it was unexpectedly terminated because of having its files deleted unexpectedly.
Apple’s change reinforces my preference for iCloud backups, and I can see it causing many people to abandon local backups and synchronization for iCloud. I’m not one to subscribe to conspiracy theories about Apple using security as an excuse to push people into paying for iCloud+, but this poorly implemented solution doesn’t instill confidence. If Apple wants to dispel such speculation, it should release iOS and iPadOS updates that eliminate the repetitious passcode requirement alongside versions of macOS that fix AppleMobileBackup properly.
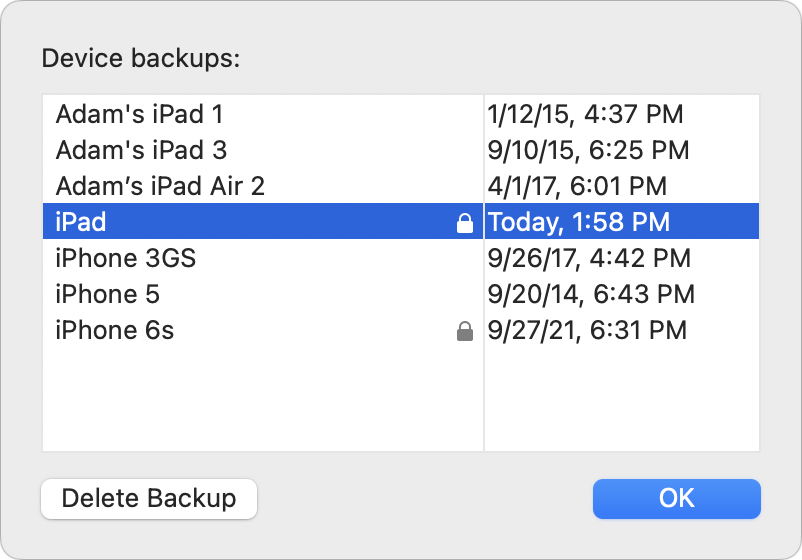
Now, if you’ll excuse me, I have to go delete those local test backups that just ate all my free disk space. Luckily, Apple makes that easy. When managing an iOS device in the Finder, click Manage Backups, select the desired backup, and click Delete Backup. (You can also Control-click a backup and choose Show In Finder to delete the backups manually.) Bye-bye, backups.
Contents
Website design by Blue Heron Web Designs