MacTalk
February 2024
Turn On Stolen Device Protection in iOS 17.3
As promised, Apple built the new Stolen Device Protection technology into the just-released iOS 17.3. It offers optional protection against a particularly troubling form of attack brought to light by reporters Joanna Stern and Nicole Nguyen of the Wall Street Journal in a handful of articles and videos (see our “iPhone Passcode Thefts” series).
In short, a thief would discover the victim’s iPhone passcode by shoulder surfing, surreptitious filming, or social engineering, then grab the iPhone and run. In some cases, criminals drugged, threatened, or attacked people to extract the passcode. Soon after, the thief would use the passcode to change the victim’s Apple ID password, lock them out of their account, and use apps and data on the iPhone to steal money, order goods, and generally wreak havoc.
The attacks worked because Apple had made resetting an Apple ID password easy for those who could only remember their passcodes. Many people forget their Apple ID passwords, so Apple decided it was worth trading some security for allowing people to recover from a forgotten password easily. It also undoubtedly reduced Apple’s customer service overhead by providing a self-service option for resetting Apple ID passwords. Unfortunately, whenever there’s a loophole or backdoor, criminals will eventually find it.
Happily, Apple now lets us eliminate that security hole with Stolen Device Protection for iPhone. It’s not available for the iPad or the Mac. Apple hasn’t explained why, of course, but there are two possibilities for the iPad. Apple may be planning to add the feature to the iPad in a future update—the iPad often lags behind the iPhone—or the company may feel that iPad users are unlikely to be targeted similarly. (Many of the reported iPhone passcode thefts took place in bars where victims weren’t paying close attention and may have been impaired by alcohol.) Macs seem even less likely to be targeted, given the additional difficulty of discovering a login password.
Stolen Device Protection Details
Here’s what happens when you turn on Stolen Device Protection. Everything works as before when you’re in a familiar location—home, work, or anywhere your iPhone has determined you use it frequently using the device-based Significant Locations system. You can change your Apple ID password, turn off Find My, access passwords in Keychain, and much more with no new requirements.
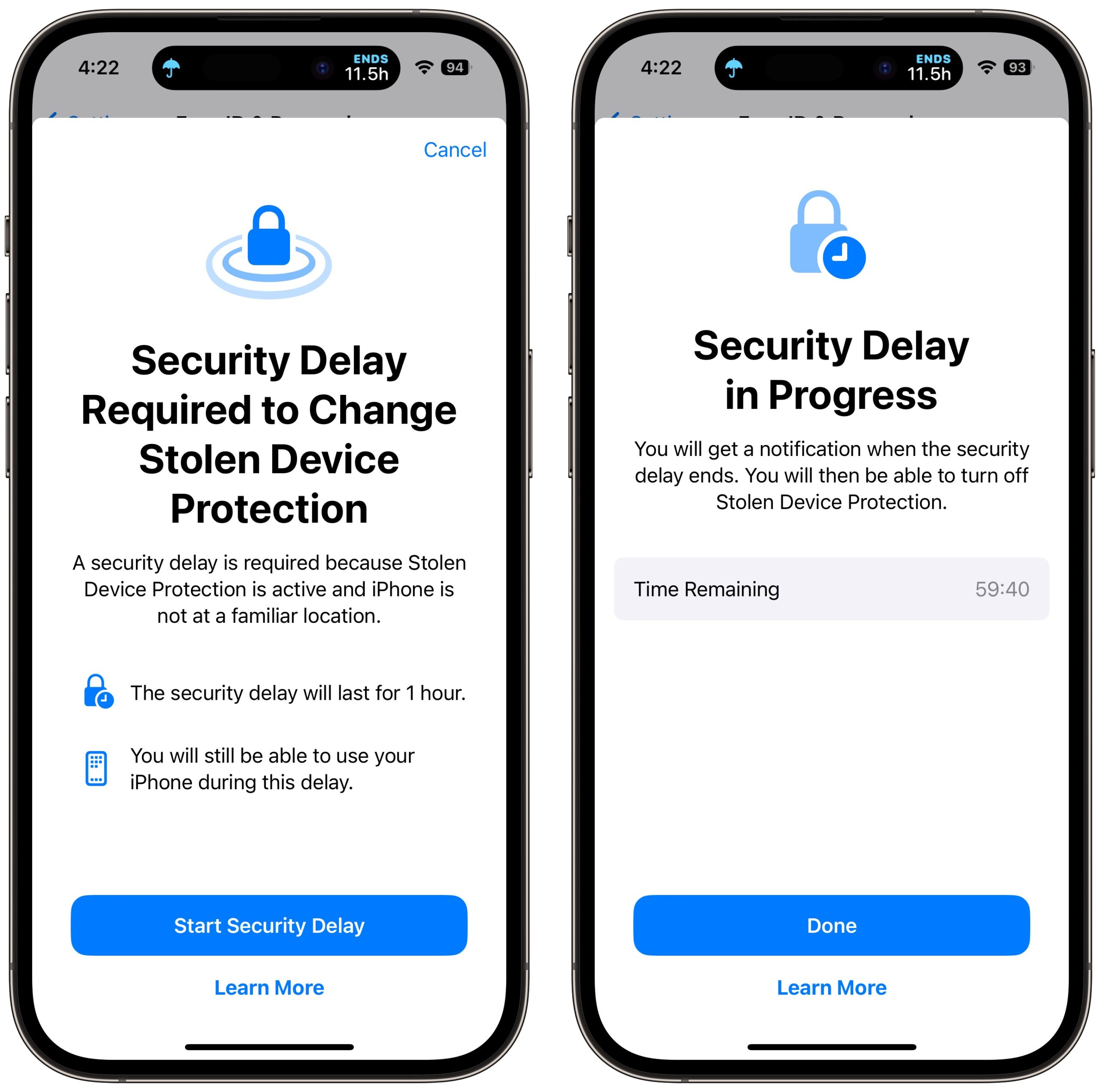
However, whenever you’re somewhere deemed unfamiliar, critical changes to your account or device require Face ID or Touch ID authentication, with no passcode alternative or fallback. The most important security actions also require a delay of an hour—shown with a countdown timer—before you perform a second biometric authentication. This delay reduces the chances of an attacker forcing you to authenticate with the threat of violence.
Apple says you must employ Face ID or Touch ID authentication in unfamiliar locations to:
- Use passwords or passkeys saved in Keychain
- Use payment methods saved in Safari (autofill)
- Turn off Lost Mode
- Erase all content and settings
- Apply for a new Apple Card
- View an Apple Card virtual card number
- Take certain Apple Cash and Savings actions in Wallet (for example, Apple Cash or Savings transfers)
- Use your iPhone to set up a new device (for example, Quick Start)
Notably, you can still use the iPhone passcode for in-person purchases made with Apple Pay, which remains a slight vulnerability. Apple likely felt that it would be too annoying to have a Face ID or Touch ID failure while attempting to pay for something at a store and not be able to fall back on the passcode.
You can also turn off Significant Locations with a passcode fallback after a biometric authentication failure, but all that does is eliminate familiar locations as a way of sidestepping biometrics. (Apple claims you must have Significant Locations enabled to use Stolen Device Protection, but that doesn’t seem to be true, and deactivating it doesn’t turn off the theft protection feature.)
Apple lays out which actions require the hour-long security delay and a second biometric authentication. These include when you want to:
- Change your Apple ID password (Apple notes this may prevent the location of your devices from appearing on iCloud.com for a while)
- Sign out of your Apple ID
- Update Apple ID account security settings (such as adding or removing a trusted device, Recovery Key, or Recovery Contact)
- Add or remove Face ID or Touch ID
- Change your iPhone passcode
- Reset All Settings
- Turn off Find My
- Turn off Stolen Device Protection
The security delay may end before the hour elapses if your iPhone detects that you’ve moved to a familiar location. In other words, you can short-circuit it by going home.
The fact that turning off Stolen Device Protection requires a security delay and biometric authentication means that you should be careful to turn it off before selling, giving away, or trading in your iPhone. Once it’s out of your physical control, it won’t be possible for anyone else to reset it.
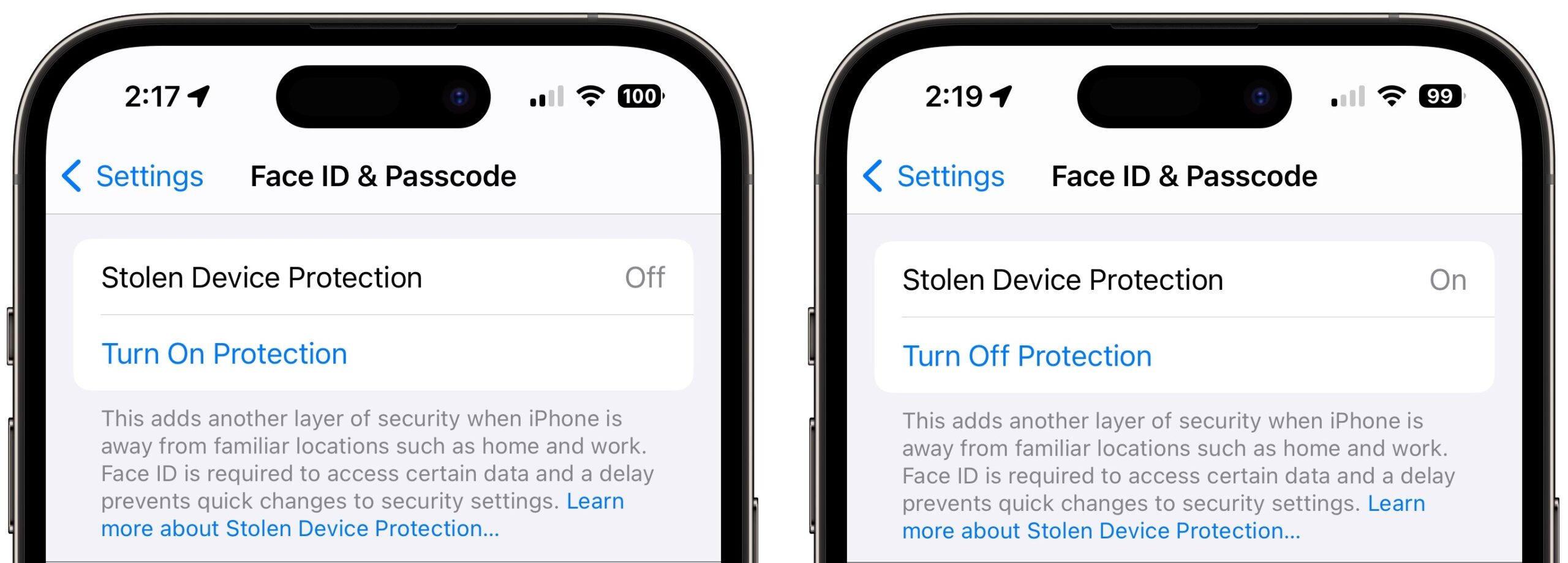
Turn on Stolen Device Protection
Turning Stolen Device Protection on is easy, and I recommend that everyone using Face ID or Touch ID do so. Go to Settings > Face ID/Touch ID & Passcode, enter your passcode, and tap Turn On Protection. (If it’s enabled, tap Turn Off Protection to remove its additional safeguards.)
Stolen Device Protection does have a handful of requirements. Apple says you must:
- Be using two-factor authentication for your Apple ID (at this point, nearly everyone is)
- Have a passcode set up for your iPhone
- Turn on Face ID or Touch ID
- Enable Find My
- Turn on Significant Locations (Settings > Privacy & Security > Location Services > System Services > Significant Locations), although this doesn’t seem to be required
Put bluntly, I can think of no good reason to avoid having all these required features enabled, anyway! With one exception, all increase your security with no privacy downside due to Apple’s careful design and end-to-end encryption. In particular, anyone who believes Apple’s biometric systems are less secure or private than a passcode is wrong and is putting themselves at risk.
The exception is Significant Locations because it displays the most recent significant location to anyone with the passcode. That makes possible—if not necessarily easy—the scenario of a thief learning your passcode, stealing your iPhone, and then going to the most recent significant location to turn off Stolen Device Protection. You would likely have more time to lock the iPhone remotely, however.
Some individuals have trouble with biometric authentication, Touch ID more so than Face ID. The inability of every iPhone user to rely on biometric authentication is one big reason why Apple made Stolen Device Protection optional. If you’re in that group, Stolen Device Protection would be problematic because it will require biometric authentication in unfamiliar locations. If you were on a trip, for instance, Stolen Device Protection and the inability to authenticate with Face ID or Touch ID would prevent you from using passwords in Keychain.
I turned on Stolen Device Protection and triggered it by turning off Significant Locations and trying to turn off various security settings. Each time, I was met with a warning dialog and a security delay. Turning the iPhone off and back on merely stopped the security delay, forcing me to restart it. When it finally expires—an hour is a long time when you’re testing!—iOS alerts you to that fact. You can then authenticate again and perform any of the previously restricted actions.
Let me leave you with one final piece of advice. It may take the criminal underworld some time before it’s common knowledge that iPhone passcode theft may no longer work, and of course, it will continue to work against those who don’t upgrade to iOS 17.3 and turn on Stolen Device Protection. So the best thing you can do to discourage possible iPhone thefts—even if they can’t ruin your digital life—is what I’ve been saying all along: Never enter your iPhone passcode in public.
Contents
Website design by Blue Heron Web Designs