MacTalk
November 2021

Add Two-Factor Codes to Password Entries in iOS 15, iPadOS 15, and Safari 15
Raise your hand if you’ve avoided enabling two-factor authentication for websites that offer it because it’s too much of a hassle to launch an app, find the appropriate site entry, copy a six-digit code and paste it in whenever the site requires that you validate yourself beyond your password. Apple feels your pain, and the company has a new streamlined way to reduce the friction in entering these short-lived codes.
Two-factor authentication significantly increases Internet security because it prevents attackers from easily hijacking online accounts. Even if you use a password manager to create strong, unique passwords for every site, passwords are still vulnerable to theft or interception. When a website’s login process requires a second factor—something you own or control, like a smartphone, tablet, phone number, or computer—you don’t have to worry about a stolen or intercepted password being sufficient to compromise the accounts.
Many sites want to use an SMS message (or a phone call) as a second factor, either defaulting to it or offering it as a secondary option. The problem is that a texted or spoken code doesn’t provide the assurance that the recipient is the party that has access—only that they have a phone number. It’s far too easy to hijack a phone number. It can be done via social engineering (talking a rep at a telecom firm into switching the number), flaws in how telecoms manage numbers, and hardware-level exploits across the telephone system.
While text and voice calls are better than not using two-factor authentication, they are relatively weak. Even as services are increasingly also supporting authentication apps or proprietary systems—like Apple’s two-factor authentication approach—many still fall back to weak SMS and voice calls.
A much better form of two-factor authentication is a shared-secret method called a Time-based One-Time Password (TOTP). Most sites that support two-factor authentication don’t require a TOTP but let you add it to an existing account. During the enrollment process, the site creates a seeding secret using its TOTP software, which it stores for your account and then shares with you. This seeding secret is typically displayed as a QR code for easy scanning, though some sites also show it as a hexadecimal-encoded number.
Setting up your side of two-factor authentication via TOTP is usually harder than enrolling at a site. You can add a TOTP secret and generate TOTPs with a standalone app like Google Authenticator (which doesn’t sync between platforms) or Authy (which does, securely), or as part of a password management tool, like 1Password. But given that only a small percentage of users rely on third-party tools, built-in TOTP support in Apple’s operating systems could drive much higher usage.
With iOS 15, iPadOS 15, and Safari 15 in macOS, that support is now in place. The updated Passwords interface bakes in the basics of password management for everyone. You work with passwords and TOTPs in Settings > Passwords in iOS 15 and iPadOS 15 and in Safari > Preferences > Passwords in Safari 15 for macOS. (Passwords won’t become a first-class macOS citizen until macOS 12 Monterey ships, at which point you’ll be able to access it in System Preferences > Passwords.) When a site or app prompts for a code later, it appears in the iOS/iPadOS QuickType bar or as an auto-fill prompt in Safari.
The ease of adding these second-factor codes and then generating them as needed should help increase usage and decrease frustration. It also makes it far easier for you to teach others how to use two-factor authentication with a minimum of fuss.
Add a TOTP
In iOS 15/iPadOS 15 and Safari 15 for macOS, once you’ve stored a password in Passwords, the easiest way to add a TOTP is with a QR code presented during enrollment:
- Go to the website or service for which you want to add TOTP verification and run through the process until you reach the QR code. (For instance, with Google, once logged in, click your image in the upper-right corner of a Web page, click Manage Your Google Account, click Security, and click 2-Step Verification. Enroll in authentication and select iPhone. You can also practice using this article, which has a non-functional but legitimate TOTP QR code.)
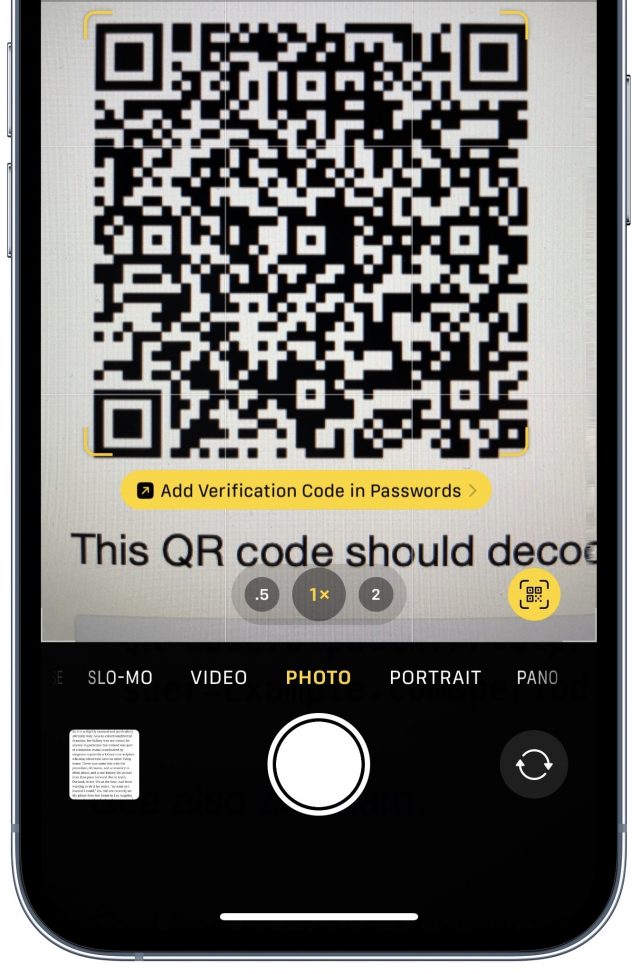
- In iOS or iPadOS, touch and hold the QR code to bring up a menu of options and tap Add Verification Code in Passwords. In Safari for macOS, Control-click the QR Code and choose Set Up Verification Code.
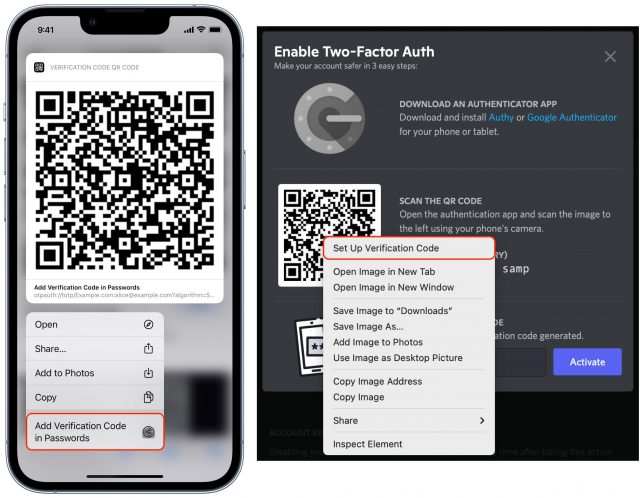
- Depending on what logins you already have stored in Passwords, you’ll be presented with one of three choices:
- A single matching account is shown, and you’re prompted to add a code to that.
- If multiple domains match, you’re asked to select or search for the correct entry.
- If no match can be found, you can search your stored passwords.
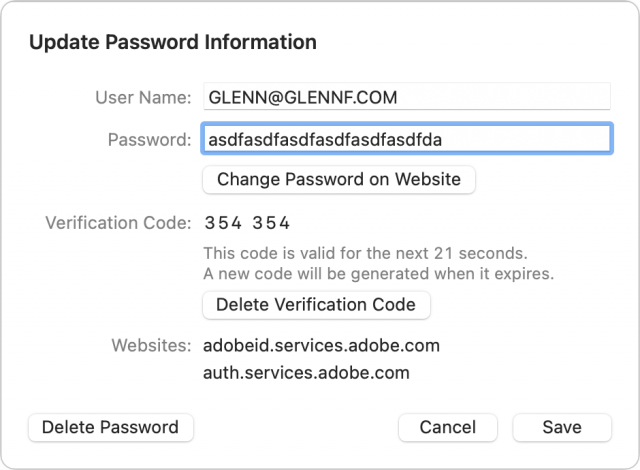
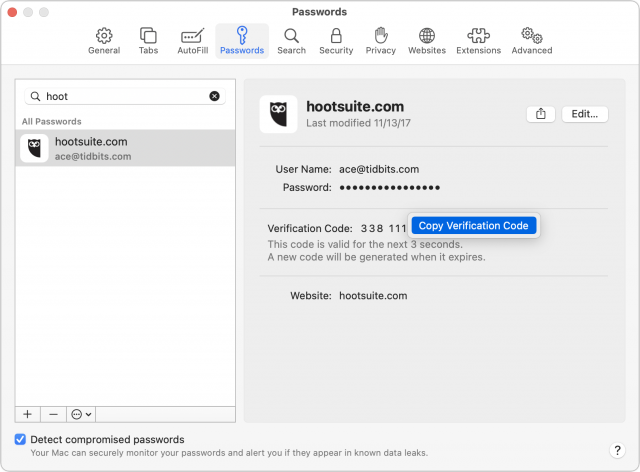
A code now appears in the Verification Code area.
If you can’t load the QR code directly within Safari in iOS/iPadOS, you can instead scan it with the Camera app, which recognizes the type of QR code and offers the same prompt as in Step 2 above.
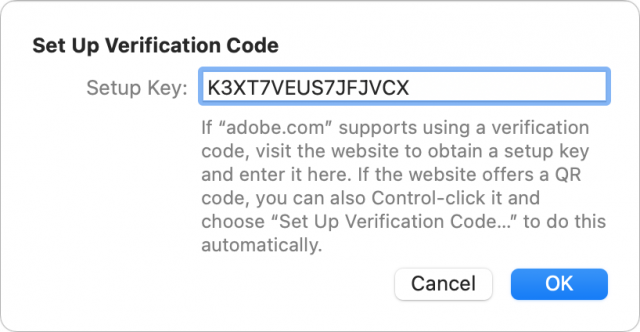
You can also set up a TOTP through other methods. Go to Settings > Passwords in iOS/iPadOS or open Safari > Preferences > Passwords in Safari for macOS. The path bifurcates here, but in both cases, you can use a TOTP’s secret if it appears on the enrollment page.
In iOS or iPadOS:
- Select a password entry.
- Tap Set Up Verification Code.
- Choose either Enter Setup Key to enter the shared secret or Scan QR Code to point at the QR Code as above.
In Safari for macOS:
After adding a TOTP, you will likely have to verify that you possess the correct code to finish enrollment.
These codes sync with the rest of a password entry’s details across your devices if you have iCloud Keychain enabled.
Unfortunately, you can’t migrate TOTPs from another app or ecosystem to Apple’s: authentication apps and systems don’t allow exporting the seed codes. Authy’s support documentation says, “In order to maintain security for our users, the Authy application does not allow importing or exporting 2FA account tokens.” Most sites also don’t let you re-display the TOTP enrollment process.
Thus, to switch from whatever you’re using now to Apple’s system, you’ll have to disable and re-enable two-factor authentication for each site or, if the site supports it, regenerate the seeding secret.
What if you want to try Apple’s system but maintain whatever app you’re using now? In that case, after you disable and re-enable two-factor authentication, you can scan the QR code or enter the setup key manually in multiple systems, one after another. Just add the QR code to Apple’s system, and then, while it remains onscreen, scan it with Authy or 1Password or whatever. You could even take a screenshot of the QR code for later addition into another app, but be sure to delete it permanently afterward, as retaining it in that unprotected form may increase your security risk.
Enter Your TOTP Code
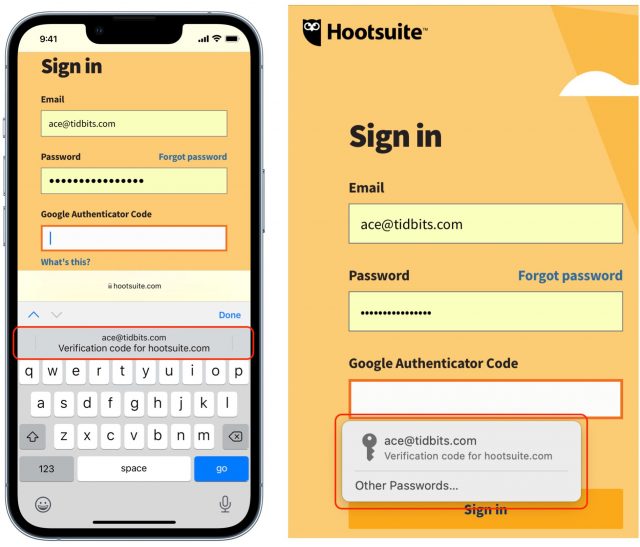
After you enter the correct username and password for an account protected by two-factor authentication using TOTP, Apple’s software automatically recognizes the field and gives you another way to enter the automatically:
- In iOS and iPadOS, Apple automatically presents a verification code option in the QuickType bar when you tap in a field requesting the TOTP code. Simply tap the item in the QuickType bar to fill the field with the six-digit code.
- In Safari for macOS, the app may automatically select the field and offer the verification code option as a button you can click, or you may need to click the field to get that auto-fill option to appear. In either case, click it to proceed.
If neither of those automated options happens, open Safari > Preferences > Passwords, find the password entry, and click the username, password, or verification code to copy them for manual pasting into the login form. Some sites make it hard to log in.
TOTPs Are Tops
TOTPs are a robust way to validate your identity as the only person who should be allowed access to an account because you’re sending a cryptographically generated code that requires possession of a secret and that doesn’t pass in a useful form through any other communication systems. The only way for an attacker to acquire a TOTP would be to hijack it from someone who can generate it and then enter the code within a minute or so—a high bar—or steal and unlock one of their devices.
Don’t make the mistake of thinking you’re not important enough to have your accounts hacked. With the seemingly constant breaches of major sites revealing millions of usernames and passwords, attackers are automating how they test which accounts they can compromise. Two-factor authentication ensures that protected accounts remain safe from this kind of wholesale attack and from many targeted ones. If you can avoid phone-based codes and rely on TOTP with Passwords in iOS 15, iPadOS 15, and Safari 15 for macOS, you’ll have the best combination of security and ease of use.
To learn more about securing your iPhone and iPad and preserving your privacy, check out the latest edition of my book, Take Control of iOS & iPadOS Privacy and Security, now updated for iOS 15 and iPadOS 15.
Contents
Website design by Blue Heron Web Designs